
Fixing Critical Vulnerability: Update Your macOS Password Manager Immediately!

Fixing Critical Vulnerability: Update Your macOS Password Manager Immediately!
A flaw in 1Password 8 for macOS may leave vault items exposed to hackers or malware. The issue, which was discovered by Robinhood’s Red Team, is resolved in 1Password 8 version 8.10.36 and later.
This issue, identified as CVE-2024-42219 , is due to an incomplete XPC inter-process communication implementation. In plain English, the thing that’s supposed to prevent untrusted apps from talking to 1Password is broken. An attacker who gains access to a victim’s Mac could impersonate a trusted app (such as the 1Password browser extension), collect security keys from the victim, and swipe the victim’s vaults.
Robinhood’s Red Team, along with 1Password itself, say that CVE-2024-42219 has not been exploited in the wild. It was also patched in the July’s8.10.36 update, meaning that very few 1Password users are currently vulnerable to the threat.
The company hasn’t specified whether CVE-2024-42219 affects 1Password 7, which a small fraction of users still cling to. That said, 1Password 7 is discontinued and no longer receives regular security updates. We do not recommend using 1Password 7.
Andrew Heinzman / How-To Geek
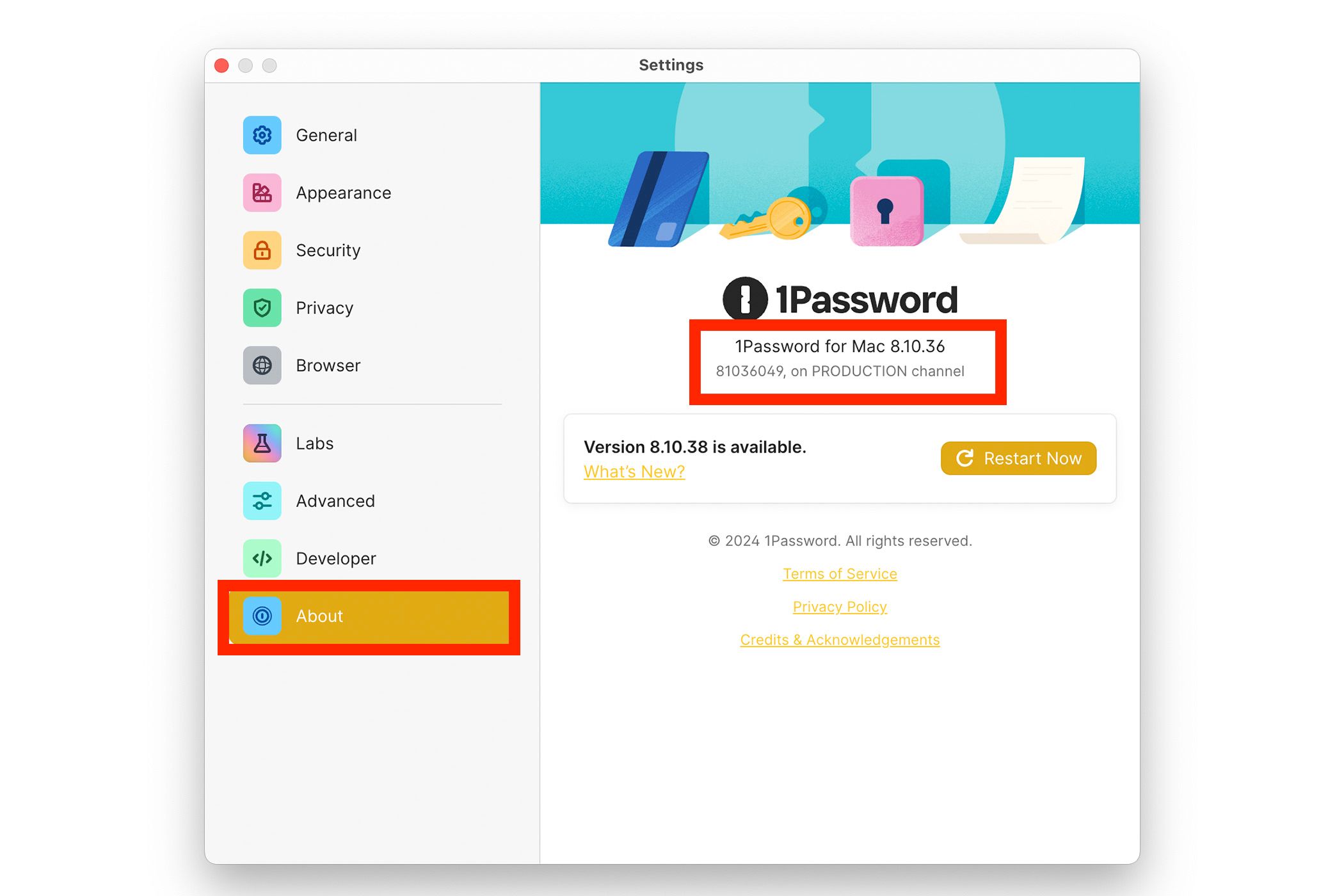
The 1Password desktop app is very good at updating itself. Still, you should check 1Password’s current version number from the “About” panel in the app’s settings (open 1Password, press Command+Comma on your keyboard, and select “About”). If you’re running version 8.10.36 or 8.10.38, you’re all good.
Auto-updates may fail if 1Password isn’t regularly used or if the app’s background processes are disabled. If you find that you’re running an outdated version of 1Password, press the “Check for Updates” button on the “About” page. Or, click “Restart Now” if the app has already detected a new update.
Note that 1Password 8.10.38 may automatically “reset some of your settings to default” as a “safety precaution.” This is due to new security improvements that were previously tested in the beta channel (and are unrelated to CVE-2024-42219). The 1Password team did not anticipate this error message, and it hasn’t specified which settings may be automatically set to default.
Source: 1Password via The Register
Also read:
- [New] GiggleGraph Make Amusing Graphics Swiftly for 2024
- [New] Hero Session Generations Compared
- [New] In 2024, Revolutionizing Facebook Advertising Through Creative Insight
- [New] Syncing Social Media Zoom and Facebook Live Interactions
- [New] X-Voice Capture Software, PC for 2024
- [Updated] A Detailed Guidance How To Add Custom Ringtones And Sounds To Your Android, In 2024
- [Updated] The Ultimate Guide for the Curious Player
- 2024 Approved Live Recording Simplified Logitech Webcam Setup Steps
- 2024 Approved Unlock the Secrets to Lengthy Exposure with iPhone
- In 2024, The Artisan's Guide to Flawless Free and Paid Software Video Downloads
- In 2024, Trailblazers in the World of Virtual Reality
- Speak the World: The Power of Multilingualism Explored
- Transform Your Pictures - The Leaderboard of Phone Sticker-Enhancers for 2024
- Title: Fixing Critical Vulnerability: Update Your macOS Password Manager Immediately!
- Author: Mark
- Created at : 2024-12-20 00:12:09
- Updated at : 2024-12-24 17:09:48
- Link: https://some-guidance.techidaily.com/fixing-critical-vulnerability-update-your-macos-password-manager-immediately/
- License: This work is licensed under CC BY-NC-SA 4.0.